Splunk Integration
You can create dashboards and alerts using k9 Security's access reports in Splunk. k9 Security's csv data formats integrate well into the Splunk security and observabilty platform.
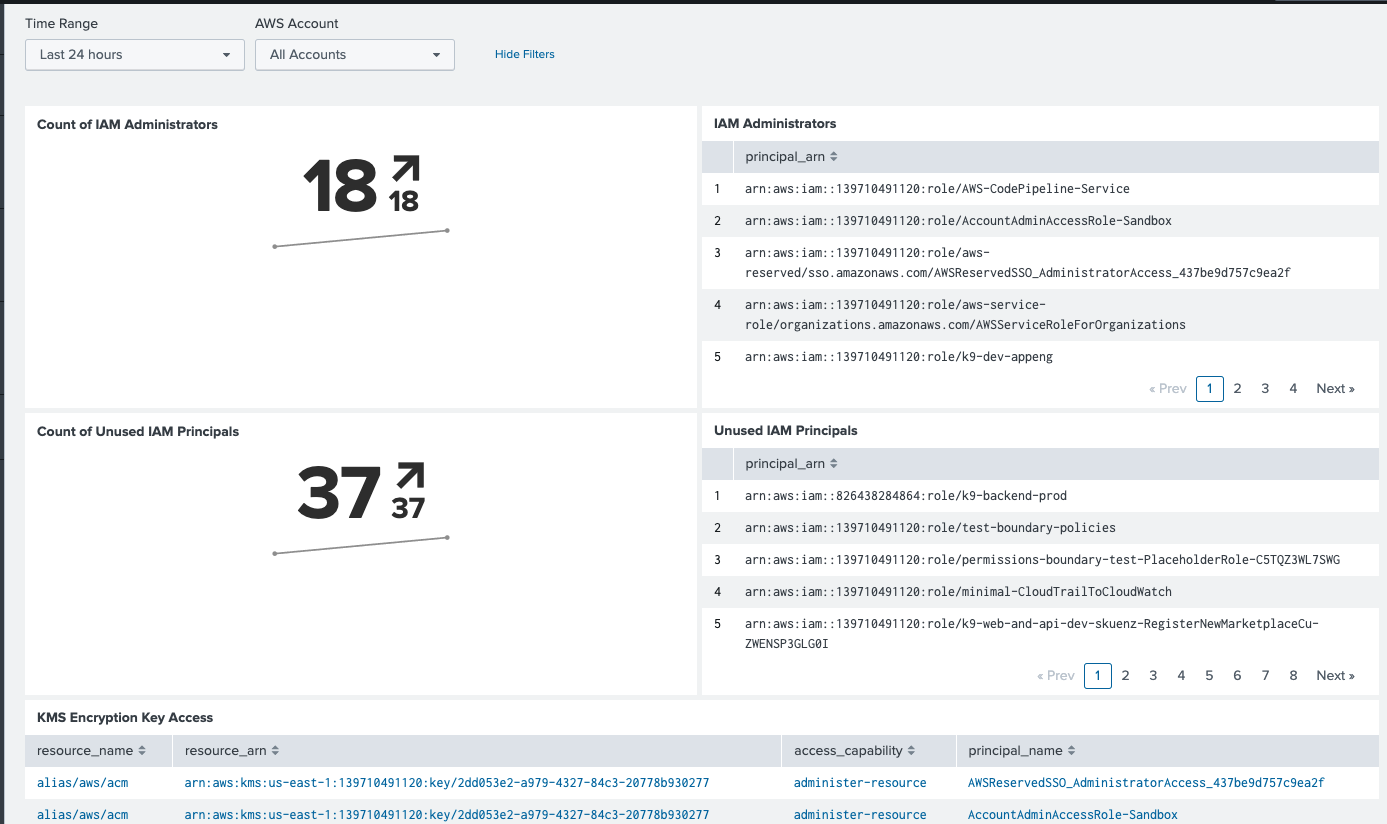
With k9 Security's access reports in Splunk, you can answer questions like:
- which principals can administer IAM?
- which principals are unused?
- which principals have the most access to S3?
- which of our critical S3 buckets are too accessible?
(Of course, we support more than just S3. You choose what goes in your dashboard.)
k9 Security provides three main components to support Splunk integration:
- a log pipeline that parses k9 Security's CSV files into Splunk events
- a (sample) dashboard to perform k9 Security's Daily Reviews
- a set of Splunk queries that automate critical AWS IAM SecOps activities by sending notable events to, e.g. Mission Control:
- Find new IAM admins
- Find stale unused IAM principals
- Find stale AWS user credentials
Getting Started
To get started, go to the k9securityio/k9-splunk-viz repository on GitHub and follow the setup instructions.
If you have any questions getting set up or querying the data, please reach out to support@k9security.io
Last update:
February 5, 2026