AWS Config Integration
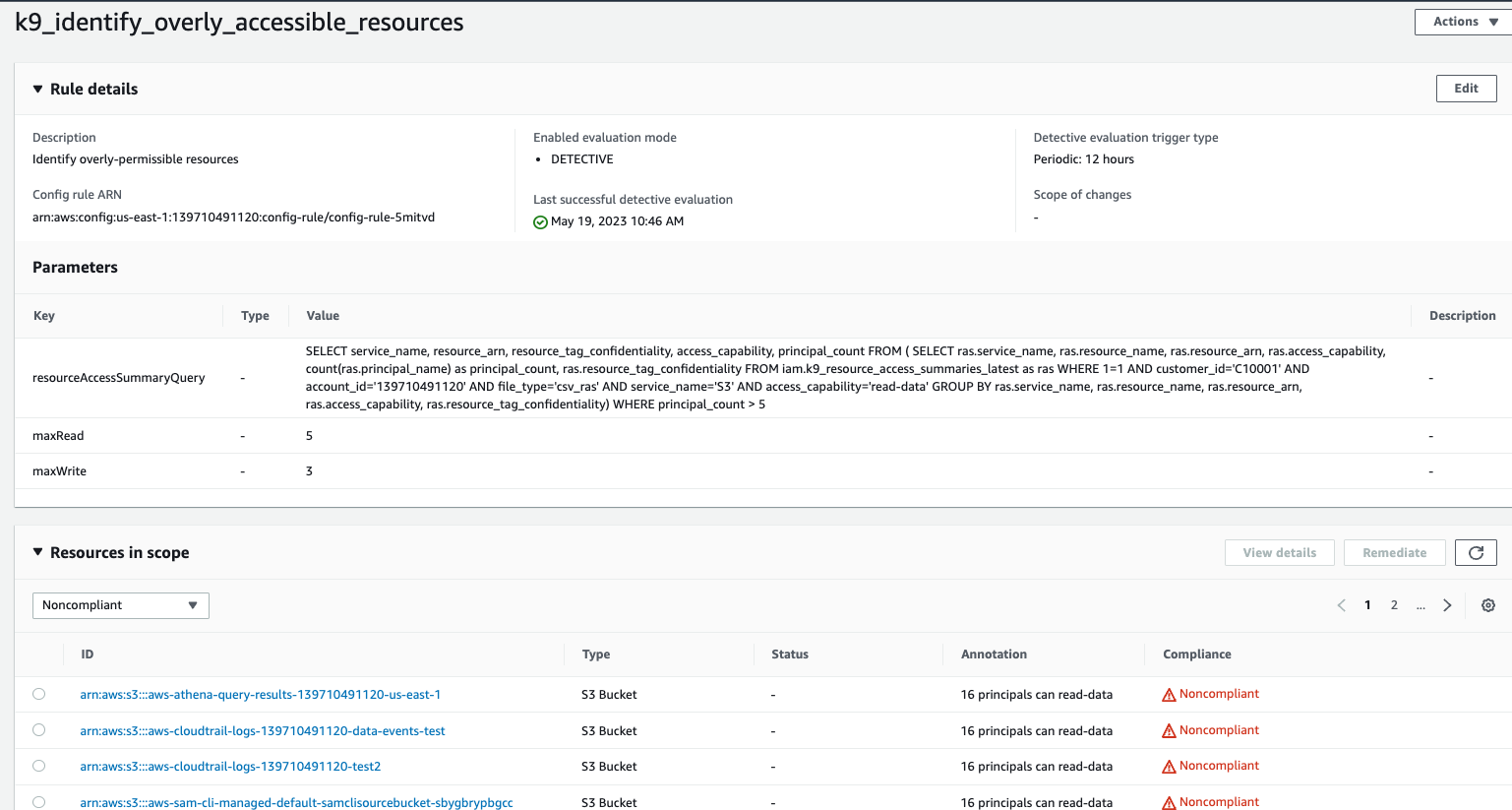
Continuously review the configuration of AWS IAM for overpermissioned principals and overly-accessible data resources using k9 Security's effective access reports and submit non-compliance findings to AWS Config. AWS Config continually assesses, audits, and evaluates the configurations and relationships of your resources.
Identify policy violations like:
- Unexpected Administrators
- Principals with Excessive Access to APIs
- Principals with Excessive Access to KMS Keys, S3 Buckets, RDS Database Clusters, or DynamoDB tables
- Overly-Accessible KMS Keys, S3 Buckets, RDS Database Clusters, or DynamoDB tables Resources
- Critical data that is deletable
Note: The AWS Config integration is currently in private preview in k9 Security's compliance solution. Contact support@k9security.io for access.
How the k9-compliance product works
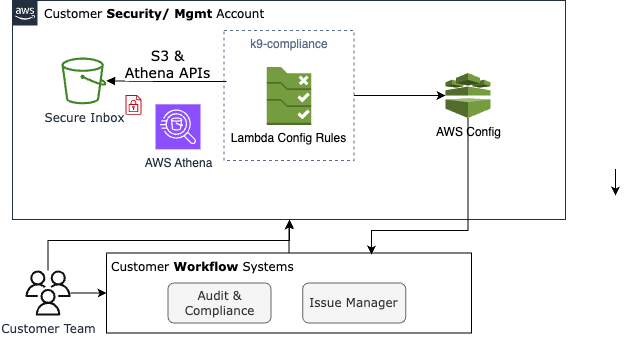
To begin reviewing your AWS IAM access entitlements continuously, subscribe to the k9 Security access monitoring service in AWS Marketplace and deploy the k9 Security Compliance Pack. Once you set up monitoring for your AWS account(s), k9 will deliver IAM access entitlements to your secure S3 inbox each night or on-demand.
Deploy the k9 Security Conformance Pack from the k9-security-conformance-pack repository on GitHub. The conformance pack will deploy:
- The Athena integration so that it can query your IAM access reports using SQL
- The default access compliance rules:
- Identify overly-accessible resources
- Identify over-permissioned principals
The rules are implemented by k9 Lambda functions deployed into your account. You can configure the rules with the specifics of your policies in three ways. You can:
- Customize the input parameters of a rule such as the threshold for how many principals having read access to a sensitive data bucket is too many.
- Define your own rules and configurations to evaluate on the k9 config functions. So you can have different rules for analyzing data classified as Classified vs Restricted.
- Create a custom function based on data returned from the k9 Athena SQL / CSVs, using our functions as a model.
AWS Config supports up to 400 rules per AWS account by default. This limit can be increased.
Once you deploy the Conformance Pack, AWS Config will evaluate these rules periodically, every 24 hours by default.